Powering Remote Work
Make working from home safe and easy

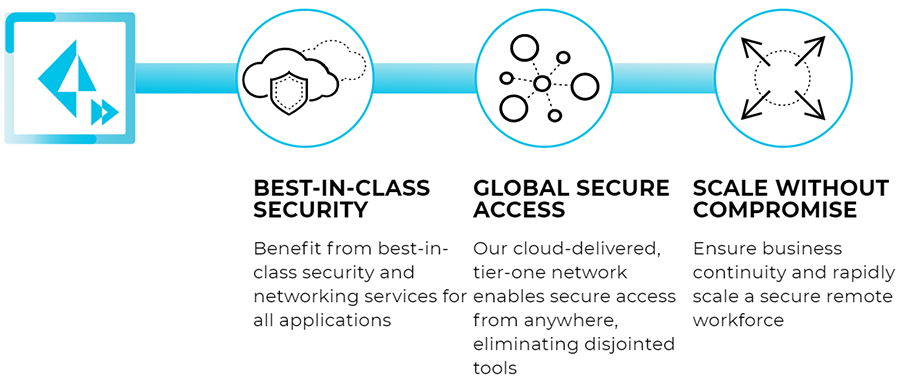
Secure Your Remote Workforce
Rapidly scaling secure remote access capacity is key as you plan to onboard large numbers of employees to work remotely with uninterrupted access and a seamless user experience. Our award-winning security with multiple deployment options allows you to securely enable your remote workforce at scale.
Connect and Secure Everything From a Single Platform
Explore various options to scale your remote access, giving you more control without compromising security.
On-Premises
Palo Alto Networks Next-Generation Firewalls support GlobalProtect, which provides an always-on secure VPN connection, enabling secure, direct access for mobile users. With full visibility and control of all application traffic, GlobalProtect prevents phishing and credential theft, protecting corporate data and sensitive information.
Cloud-Delivered
Prisma Access is a Secure Access Service Edge (SASE) that helps organizations enable secure remote workforces from the cloud by providing consistent security services. Based on a common cloud infrastructure, Prisma Access delivers protection from over 100+ locations around the world in 76 countries. Prisma Access dynamically scales to meet user throughput demands, helping ensure business continuity.
Times Are Changing for Remote Access
What’s the Difference Between Remote Access and VPN?
Remote access VPN has been a staple for large enterprises for years, and it’s easy to understand why many people think that “remote access” and VPN are synonymous with one another. I often find it’s useful to have a discussion about the terminology before diving into what the requirements are for securing today’s application mix.
“Remote access” is a use case, and it’s very specifically referring to the scenario when an off-prem user, sitting on an external, untrusted network, needs to reach internal applications in the data center. Users are remotely accessing internal resources.
VPN is the tunneling method used to make remote access possible across a broad range of applications, over all ports and protocols. VPN provides the encrypted connection for privacy, but it does not provide the traffic inspection for visibility and security. However, the majority of remote access VPN deployments are based on a hub-and-spoke topology because the user is trying to reach an internal data center. Therefore, the traffic can be inspected by the corporate firewall. Both the networking team and the security team are on common ground, given that the networking path is optimal and the security is in place.
Shifting Applications to the Cloud
What happens when applications shift to the cloud? Now, both the mobile user and the application are off-prem, and “remote access” is only one use case. Access to the cloud is also necessary and increasingly more important. That’s when architectural differences of opinion start to crop up on how to build out the right security to support different networking requirements. Cloud and networking teams would both argue (quite correctly) that it doesn’t make sense to send traffic over a hub-and-spoke network just to reach the internet egress point at headquarters. Therefore, instead of remote access VPN for these use cases, many organizations are using other types of access approaches to cloud and internet applications, such as CASB for SaaS cloud access proxy for public cloud/internet web access.
New types of issues crop up because controlling access isn’t the only security issue. Inspection of traffic, using three different inspection methods with variations based on which application is being used and where the user is located, is not a good idea. It’s even a worse idea when you consider that both CASB and proxy do not secure all traffic, and anything less than full inspection of the traffic leaves open-ended questions about what happens to the uninspected traffic. Is it benign; is there C2 communications over non-standard ports; or is data being exfiltrated out of a compromised endpoint?
Therefore, full tunnel traffic, properly inspected across all ports and protocols, is the right thing to do from the perspective of security; it’s just that remote access VPN is the wrong way to do it. You can’t build a cloud-focused application strategy around a hub-and-spoke topology. A modern approach requires a new architecture.
Using GlobalProtect Cloud Service as Your Security Architecture
With GlobalProtect cloud service, mobile workforces gain access to all of their applications, whether to the public cloud, SaaS or the internet. All users, no matter where they are, are consistently protected in the same manner. Whenever a user has access to the internet, the GlobalProtect app (on the user’s laptop, mobile phone or tablet), automatically establishes an IPsec/SSL VPN tunnel to GlobalProtect cloud service. The traffic receives full inspection across all ports and protocols, including encrypted SSL/TLS traffic, no matter whether the application lives in the public cloud, private cloud or on the internet. With security policy defined on traffic classification based on App-ID, organizations can further specify access policies based on User-ID, and Host Information Profile as well as consistently enforce protections against exploits, malware, credential theft and other cybersecurity threats.
As you look at your mobile workforce strategy, think about how to use the GlobalProtect cloud service as your security architecture. Instead of being tied down to the architectural limitations of remote access VPN, use GlobalProtect cloud service to move your networking and security forward with support for all of the applications your users need.
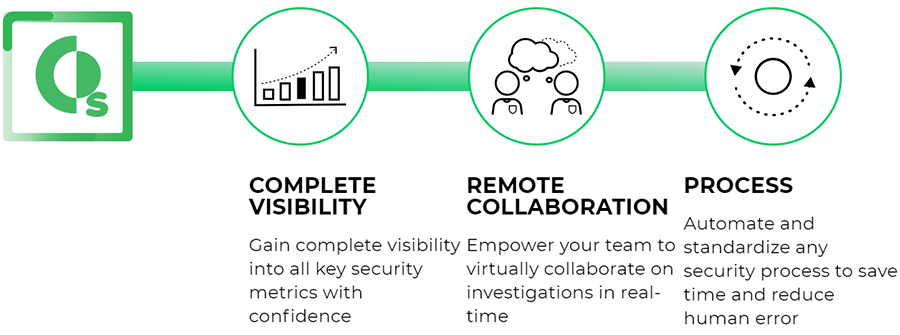
Remote Security

Securing your remote workforce
How to go from 20% to 100% remote overnight with Prisma Access and GlobalProtect.
See how next-gen technology impacts cybersecurity:
![]()
Remote security, together as one
Get best-in-class orchestration and automation capabilities with Cortex™ XSOAR.
See how next-gen technology impacts cybersecurity:
Strata Secure the Enterprise
Palo Alto Networks Strata
Prevent attacks with the industry-leading network security suite, which enables organizations to embrace network transformation while consistently securing users, applications, and data, no matter where they reside.
Prisma Secure the Cloud
Palo Alto Networks Prisma
Prevent attacks with the industry-leading network security suite, which enables organizations to embrace network transformation while consistently securing users, applications, and data, no matter where they reside.
Need help? Chat with an industry expert right now!
Please fill out the form below or call us at
(02) 9388 1741.
Contact Us
Sydney Office:
PaloGuard.com.au
A division of Virtual Graffiti Australia Pty Ltd
Darlinghurst, NSW, 2010
Australia
Telephone:
- Local: (02) 9388 1741
- International: +612 9388 1741
[email protected]
Normal Business Hours:
- Mon - Fri, 8:30am - 6:00pm AEST/AEDT
Our team is here to help you! We are available from Mon - Fri, 8:30am - 6:00pm AEST/AEDT and attempt to respond to all inquiries within 1 business day.
Please Note: Technical support is provided by the manufacturer. If you have a product support related questions, please contact the manufacturer directly.